Blockchain Advances based on Game Theory and Cryptography
work combining cryptology and game theory properly. Similarly, even
though many blockchain-based applications have been proposed recently,
most of them lack proper analysis based on cryptography, game theory,
and distributed systems perspectives. The main novelty and benefit of
our project is the fact that it is among very few works that combine
cryptology and game theory, as well as apply this combination
methodically on the blockchain. We address the following topics:
* Blockchain and Smart Contract based Outsourced Cloud Computation
* Lightweight, Fast, and Scalable Blockchain based on Distributed Hash Tables
* Securely Updatable / Redactable Blockchain
* Decentralized Anonymous Online Donation System.
We are grateful for the support from TÜBİTAK.

Password-Based Authentication
We are grateful for the support from the Royal Society Newton Advanced Fellowship.
Social Network Privacy
Our solutions provide cryptographic guarantees on the confidentiality of our profiles, habits, comments, photos, etc. We also have solutions for secure authentication using social networks with the fourth paradigm of authentication: “Someone You Know“.
We are grateful for the support from TÜBA (Türkiye Bilimler Akademisi – Turkish Academy of Sciences).

Searchable Encryption
Our solutions work with dynamic data (both keywords and documents can be efficiently changed, added, removed), providing security against fully malicious servers, under both random oracle and the standard model. We also provide forward privacy: if a document is added containing a previously searched keyword, many existing solutions leak this information, while our solution does not leak such additional information.
We are grateful for the support from Bilim Akademisi (Science Academy) and TÜBİTAK.

Secure Cloud Storage
Using our techniques, both users and companies will benefit. Users will enjoy increased security and provable cryptographic guarantees, while companies can charge premium fees for offering such guarantees, or bring more customers who were worried about security issues. We hold several patents on this topic.
We are grateful for the support from Koç Sistem, Türk Telekom, TÜBİTAK, and European Union COST Action IC1206.

Cloud Computation
- P2P (peer-to-peer) cloud: Outsourcing the job to multiple entities
- Giant cloud: Outsourcing the job to a more powerful entity (e.g., Amazon EC2)
Cloud computing presents unique challenges that need to be addressed by cryptography and security experts, as well as game theory and mechanism design principles. Our goal is to combine different techniques to ensure result reliability and inline participation incentives. Further goals may include computation privacy, such as privacy of queries and data in outsourced databases.
We also have efficient solutions for fair and secure two-party and multi-party computation (2PC and MPC). These solutions enable two or more parties to compute a function together, where each party provides some input, but the other parties do not learn any useful information about that input (except, of course, the output of the function). We enable such protocols to be done fairly efficiently, where either all parties receive the output of the computation, or no one receives anything useful.
We are grateful for the support from TÜBİTAK and European Union COST Action IC1306.

Outsourced Databases
- Complete: There is no extra record added to or no missing record removed from the result.
- Correct: All records in the result remain unmodified.
- Fresh: The result only contains the latest versions of the records in a dynamic database.
We also separate the job of the regular database management system (DBMS), and the database authentication system (DBAS). We leave the DBMS unmodified, and introduce a DBAS system that can work with any DMBS solution. We further let the data owner and queriers to be different parties.
We are grateful for the support from TÜBİTAK.

Fair Exchange
There has been a great deal of research on fairly exchanging two items. But when one considers peer-to-peer systems, efficiency and performance of the fair exchange protocol matters. We created an efficient and scalable optimistic fair exchange protocol suitable for use in high-churn peer-to-peer file sharing systems. Our fairness solutions are also applicable to scenarios including secure two-party or multi-party computation, as well as cloud storage systems.
Furthermore, while analyzing the limits of fair exchange protocols, we looked at distributing centralized parties, such as the trusted third party, the arbiter. Our results include impossibility cases and optimality proofs.
We are grateful for the support from TÜBİTAK and European Union COST Action IC1306.
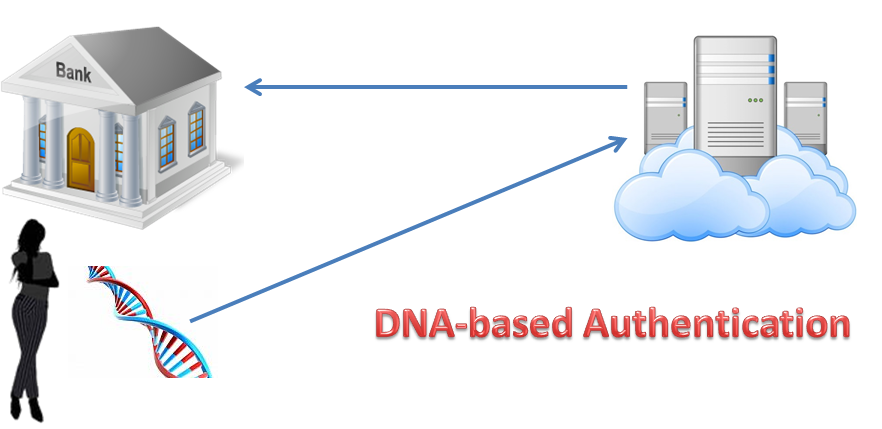
Genetic Authentication on the Cloud
We are grateful for the support from TÜBİTAK through 1003 Large Scale R&D program. This project is done in collaboration with:
-
Erman Ayday, Bilkent University
-
Hüseyin Onay, Ege University (PI)
-
IDEA Technology, İstanbul


Future Projects
- Usable Security, Password-based Authentication, One-time Passwords, Dictionary Attacks
- Peer-to-peer systems, including video streaming, storage, distribution, and their security
- Database Privacy, Private Information Retrieval, Privacy-preserving Information Sharing
- Private Health Information Sharing, Electronic Health System record privacy
- Cryptocurrency systems, Electronic Cash, Anonymous Credentials, Bitcoin, Blockchain
- Electronic identity systems (e-ID and e-passport), Anonymous Authentication, Public Key Infrastructure (PKI)
- Novel applications with Lattice-based cryptography
- Novel applications with Elliptic-curve cryptography
Contact us with a research proposal if interested. See the Work with Us page.
